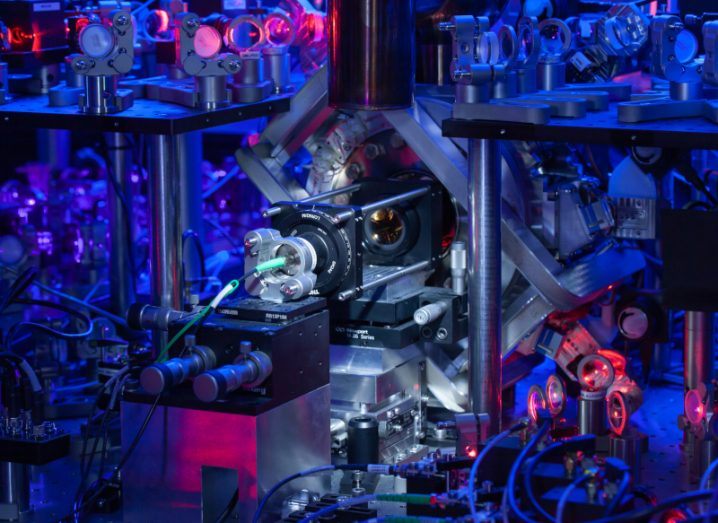
Researchers hope that their method will now help generate secret keys with uncharacterised and untrustworthy devices.

In today’s world of growing internet usage, various complex encryption techniques are used to secure crucial data and to make sure that it is only accessible to the rightful owner. However, with the rapidly advancing technology, it is possible that futuristic quantum computers could crack through this shield in no time. In order to bolster the security, researchers have implemented an advanced form of quantum cryptography which would make the encryption immune to hacking. While quantum key distribution (QKD) is not affected by attacks on the communication channel, the manipulations in the devices can do the harm.
In the case of device-independent QKD or DIQKD, the cryptographic protocol is not dependent on the device used. For the exchange of quantum mechanical keys, either light signals are sent to the receiver by the transmitter or entangled quantum systems are used.
In the new study, published in Nature, scientists conducted an experiment where they used two mechanically entangled rubidium atoms. They excited both particles with a laser pulse and after which they fell into their ground state while emitting a photon in the process.
In the protocol, developed by researchers at the National University of Singapore (NUS), two measurement settings for key generation are used rather than just one. “By introducing the additional setting for key generation, it becomes more difficult to intercept information, and therefore the protocol can tolerate more noise and generate secret keys even for lower-quality entangled states,” said Charles Lim from NUS. Lim is also one of the authors of the study.
In conventional QKD methods, security can be guaranteed when the quantum devices used have been characterised well. “And so, users of such protocols have to rely on the specifications furnished by the QKD providers and trust that the device will not switch into another operating mode during the key distribution,” explained Tim van Leent, one of the lead authors.
Researchers hope that their method will now help generate secret keys with uncharacterised and untrustworthy devices. They are now aiming to expand the system and incorporate several entangled atom pairs.
[Source=gadgets360]







Leave a Comment